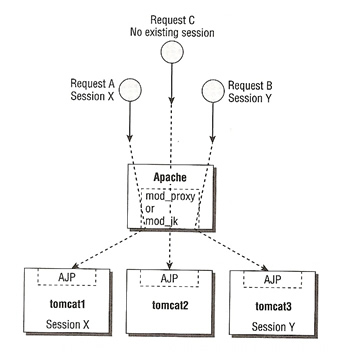
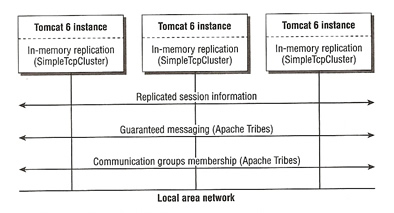
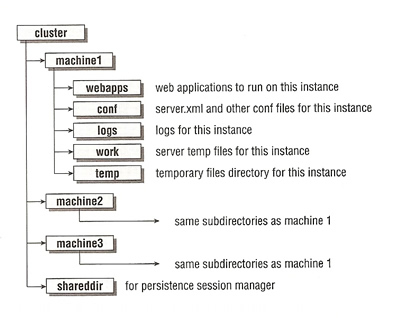
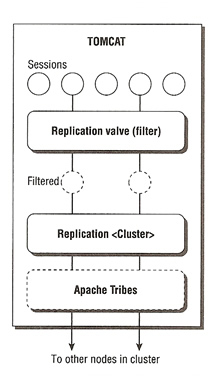
What
STD is a Linux-based Security Tool. Actually, it is a collection of hundreds if not thousands of open source security tools. It's a Live Linux Distro, which means it runs from a bootable CD in memory without changing the native operating system of the host computer. Its sole purpose in life is to put as many security tools at your disposal with as slick an interface as it can.
Who
STD is meant to be used by both novice and professional security personnel but is not ideal for the Linux uninitiated. STD assumes you know the basics of Linux as most of your work will be done from the command line. If you are completely new to Linux, it's best you start with another live Distro like Knoppix to practice the basics (see faq).
STD is designed to assist network administrators and professionals alike secure their networks.
The STD community is extremely active. Come and join us on the forum here